Since the Internet’s inception, we’ve dealt with a plethora of cyber security issues. Before we finish investigating one threat, five more pop up. Every minute, over 1000 people are hacked worldwide, and as such, according to The Ethical Hacker, we are not very safe at all. But there’s light at the end of the tunnel! Not everything is so grim. Cue in secure shell (SSH).
Let’s dive into a brief history.
Someone hacked a Finnish university network by installing a password sniffer into a server. This data breach gave the hacker thousands of usernames and passwords in the database. When it was discovered, it was both terrifying and inspiring. In 1995, Tatu Ylonen, one of the hacked victims, created the Secure Shell protocol.
Ok, so what does it do?
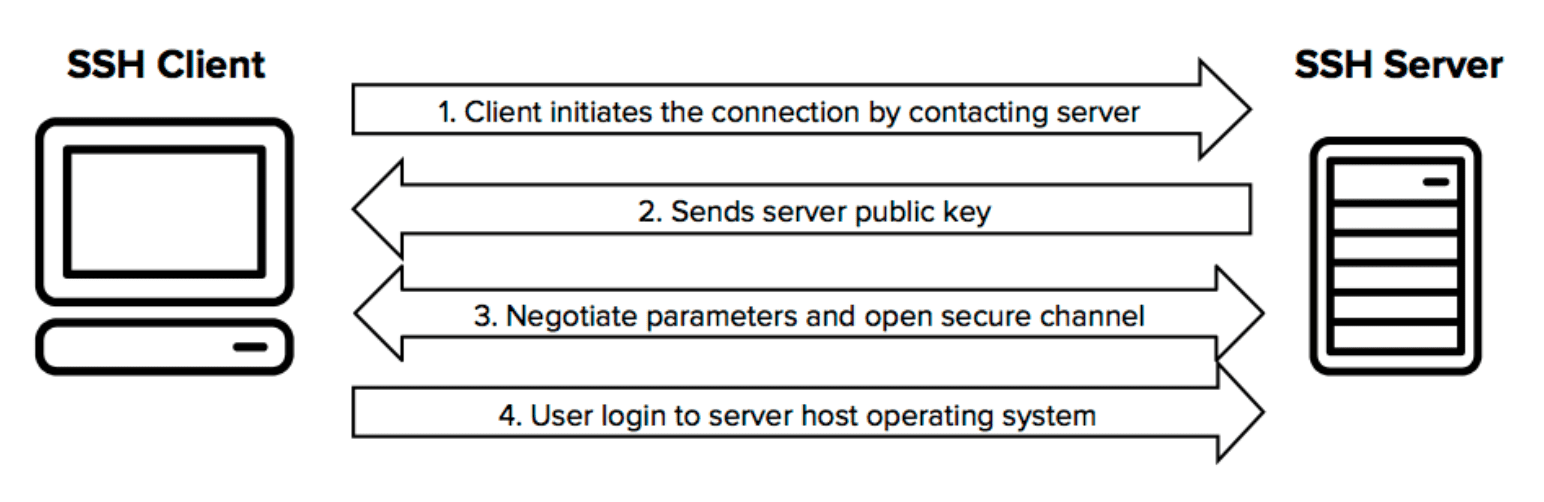
Simply put, secure shell enables us to log into a computer remotely, execute commands, and transfer files securely.
There are many different secure shell commands and implementations that can be used. Constantly, new updates are made as the open source community continues to use SSH. A common alternative to SSH that’s often used for similar purposes is File Transfer Protocol. FTP is used to copy files up to a server. That’s an insecure protocol because passwords get sent in plain text, unencrypted. Instead, we use SSH to connect to the server and work directly on the server at a text-based command prompt. By typing commands, we’re controlling the server somewhat like you would control your computer using a keyboard and mouse.
The most basic use of SSH is for connecting to a remote host for a terminal session. The form of that command is: ssh UserName@SSHserver.example.com
At Buckeye Interactive, all of our developers use secure shell “all day, every day,” as one of our software engineers puts it. SSH lets our devs do things like manage servers for our clients. It also allows us to write code directly on our dev servers, so we don’t have to set up our own computers to run the code, just the servers. Basically at any point in the day, any one of our developers will have at least 1 (if not 5-10) secure shell sessions running.
To reiterate, SSH is extremely effective in diminishing security threats to different networks and servers. All of the communication between the client and the server is encrypted. Because of this, secure shell is deployed on millions of servers and is used in almost all data center environments.
If you have any further questions about SSH, please comment below! And as always, if you need help building solutions for your business, start a project with us!